Email Impersonation is where an attacker sets up an email address to look like another legitimate email. It is similar to other attack methods which require a little more technical ability, like
- Email Spoofing – where an attacker modifies the email headers so your mail client will display a false email address
- Account Takeover – where an attacker gains access to another person’s account and uses it to send phishing emails.
Email Impersonation, Email Spoofing, or Account Takeover attacks will generally fall into these categories
- Business Email Compromise – Impersonating a Business
- CEO Fraud – Impersonating a company executive (or HR, IT etc) to target an employee
- Whaling – Targeting a company executive or other high-profile account
With email impersonation and spoofing, all the attacker needs is an email address they believe they can pass off as something it’s not. It requires very little in the way of cost to setup and is quite easy to do. This is what we will focus on in this article.
Types of email impersonation
For this, it’s handy to understand the different parts of an email address. We’ll start at the end and work our way backwards.
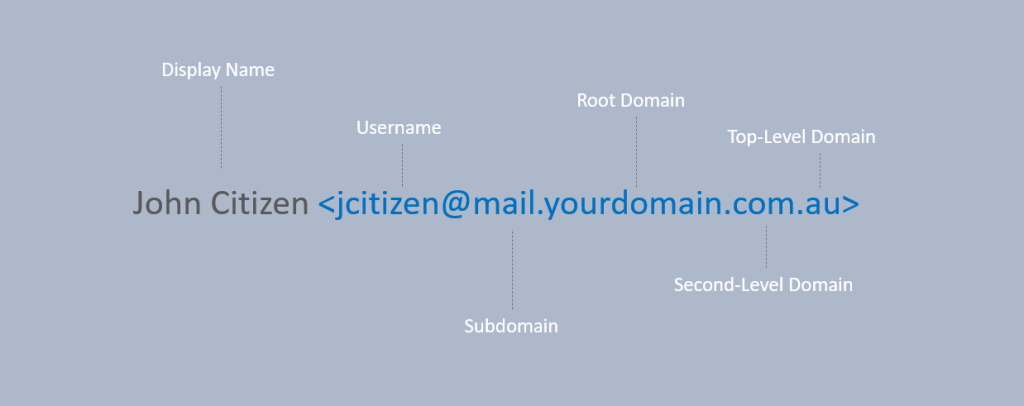
Top-Level domain-based email impersonation
Here we are looking at the very right of the email address, after the root domain. The Top-Level Domain, or TLD, usually denotes the country or type of organisation (com, gov, nz, au). This is sometimes accompanied by a second-level domain (com.au, co.nz, net.au, gov.au). Using top-level domain impersonation an attacker would create an address that you might believe is legitimate but is coming from a different TLD than the one you might be expecting.
email coming from expecteddomain.io instead of the genuine expecteddomain.com.au
Root domain-based email impersonation
This is normally the most distinctive part of the email address, the part immediately before the TLD. An attack using this method normally involves registering a domain that has some character substitutions. Think 1 in place of I, 0 for o. Multiple characters posing as one, rn for m, cj instead of g, cl for d. Alternative accepted glyphs may also be used in place of characters too, ø.
Subdomain-based email impersonation
The subdomain is anything between the @ and the root domain – most email addresses won’t have a subdomain. An attacker might employ them in these two main ways.
- Using a company name as the subdomain: eg@expecteddomain.gmail.com
- Splitting a company name across the subdomain and root domain: eg@expected.domain.com
Username impersonation
The username is the part of the address before the @. This signifies the account on the domain the email is being sent from. An attacker using this type of attack will often register an address with a free email provider with an account name that they can pass of as a known employee. Most commonly they will attempt to register an account with a username in line with their target’s CEO or other high-profile user. They may also use some of the character substitution tactics outlined above in Domain-based email impersonation, if the name has already been registered. For example, if you have a high-profile user with the name “Matthew Farris” you might be on the lookout for things like:
Matthew Farris <mathewfarris@emailsomething.com>
Matthew Farris <mfarris@freeemail.com>
Matthew Farris <matthewfarrls@gmail.com>
Display name impersonation
Finally, we come to the display name, this is the name you choose when you create your email account and could have nothing to do with the username. For example, anyone can register an @gmail.com address and send email using a display name that is completely different to the username. On most mobile email clients, the sender will default to display the display name only so be careful.
Direct Spoofing
This requires a little more sophistication from the attacker but is something we are seeing more and more of. The attacker modifies the email headers when they are sending their message so that your mail client will display the address the attacker has chosen rather than where they have actually sent it from. This is often a little more difficult to detect. Often you can tell by paying close attention to the overall tone and content of the email as well as applying a healthy dose of scepticism. Other times, you may not be able to tell unless you dive deep into the email headers to try to determine if the sending server acts as a legitimate sending server for that email domain. By implementing Domain Name Server records like SPF, DKIM, and DMARC together; you can help prevent your domain from being used in this way against your staff, your contacts, and your clients.
Weird outlier to be on the lookout for
+ aliasing
Some email accounts allow for + aliasing. This is useful for when someone wants to utilise mail filtering for messages they receive. Sign up to a service using a +aliased email address and build a mailbox filter to sort received communication directly to a folder. This could also be used to impersonate individuals and so it is important to know which address is the controlling address. The username before the + is the real sender, anything between the + and the @ is decoration.
IT Support <it_supporl+youritfirm@gmail.com>
Your Client <notyourclient+yourclient@gmail.com>
General recommendations
Always check the sender info, look for the impersonation tricks listed above. Regard the overall tone and format of the message. Ask yourself, is this communication expected, is it in line with previous communication received, is it trying to get me to do something, is it appealing to a sense of urgency, these can all be indicators that something is amiss. If in doubt, call (using a known or verifiable number) and confirm if the communication is genuine.
Further reading:
Use DMARC to validate email, setup steps – Office 365 | Microsoft Learn